Internet 101 : How to Stay Safe Online

Continuously think before you Share Something
Social Networking sites like Facebook are an extraordinary spot to associate with loved ones on the web. Notwithstanding, it is additionally simple for individuals to share individual data about themselves or others. Before sharing something, ensure it is something you wouldn't see any problems if everybody saw. All that you share on the Internet ought to be thought of as open to the public since it is workable for something you accept is shared secretly to be leaked out freely. In case you're contemplating sharing something that you think could irritate somebody or humiliate you, perhaps consider not putting it on the Internet.
Don't Always Believe What You Read on the Web
Understand that it's feasible for anybody to make a site on the Internet and that somebody may just make a website for bad intentions. For instance, a site could be made to help spread dread, lies, or malware.
Utilize a Secret Password
Avoid the self-evident. Never utilize successive numbers or letters , think about utilizing a secret key manager.
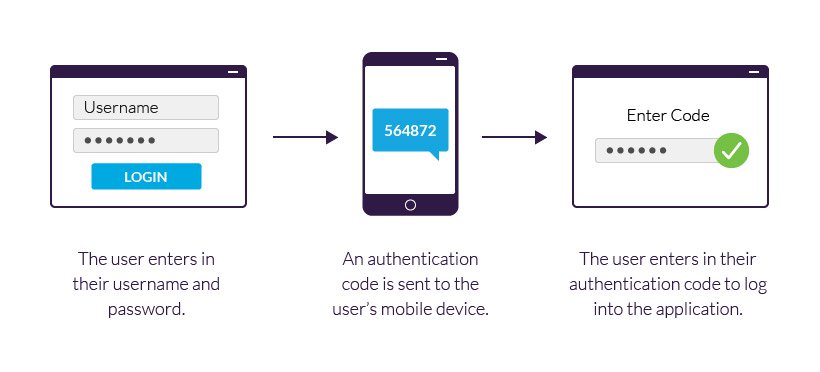
When accessible constantly empower two-factor authentication
Two-factor confirmation includes extra insurance by requiring an extra advance in checking a login.
Update your System and Softwares
Alot of the updates that are released by develeoper are identified with PC security-related issues. Ensure your perating System is continually running the most recent updates and that you're running an operating system that is as yet supported by the developer/engineer. More seasoned OS like Microsoft Windows XP are never again bolstered by Microsoft and consequently never again get updates
Confirm if the Webites Encryted or Not
To confirm this, search for a little lock (Internet program security lock) symbol in the base right corner of your program window or by the location bar. On the off chance that unmistakable, the lock symbol ought to likewise be in the bolted position and not opened.
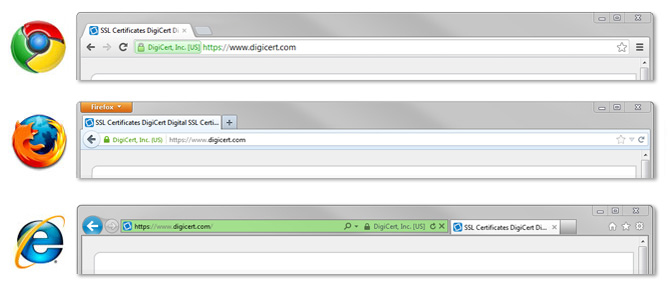
URL starts with https, as appeared previously.
Know about phishing tricks
Acclimate yourself with phishing tricks and procedures, which are utilized to fool you into revealing your record data. Web based financial banking, Paypal, eBay, Amazon, and other famous locales that require logins are mainstream targets.
Continuously be Mindful of Email Connections and Links
One of the most well-known strategies for spreading infections and malware is through email connections and hyperlinks sent through email. Continuously be incredibly mindful when managing any connections or links in messages you've gotten from anybody (even loved ones).
Always be Cautious when Accepting or Consenting to Prompts
At the point when you're incited to introduce any program or add-ons, try to peruse and comprehend the agreements before tapping on the Ok button. On the off chance that you don't comprehend the understanding or feel it isn't important to install the program, drop or close the window.
Furthermore, when installing any program, watch for any check box that inquires as to whether it's alright to install an outside program, toolbar, and so on. These are rarely required and frequently cause a bigger number of issues than great. Leave these cases unchecked.
Be Mindful Where you're Signing in from Business Areas
Your work environment can install key loggers or utilize different strategies for checking the PC while on the web. Somebody who access this data could peruse these logs and collect usernames and passwords. Additionally, don't store any passwords in your program if your PC is imparted to other workers.
Friend's Home
Be concerned when signing into a record on a companion's PC. A PC or system you are curious about could deliberately or inadvertently log usernames and passwords. At last, when signing into any site on a companion's PC, never spare the secret word data on their program.
Utilize an Alternate Internet Browser
![]()
Old versions of Internet Explorer are not secure. On the off chance that you are utilizing Internet Explorer as your program, consider an alternate program, for example, Google Chrome or Mozilla Firefox. On the off chance that you are running Windows 10 and need to keep on utilizing a Microsoft program, consider utilizing Microsoft Edge rather than Internet Explorer.
Update Internet Program Modules or Plugins
Frequently numerous attackers discovers security vulnerabilities through program modules, for example, Adobe Flash. Ensure all intalled Internet modules are up yo date
Secure Passwords
Make sure to store passwords and login data in a protected area. Never write login data on a sticky note or in a text file that isn't encryted.
Ensure yourself Against Malware, Spyware, and Viruses
Shield your PC from viruses by installing an antivirus program on the PC. On the off chance that you would prefer not to install antivirus and your PC is running a more up to date version of Windows, at least have Windows Defender running on the PC. Additionally, having a malware protection program on the PC, for example, Malwarebytes, is likewise a decent technique for securing your PC against malware and spyware.
Confirm the Checksum of Downloaded Records
Chances that you've downloaded a program from a site that likewise records a document checksum, ensure the checksum coordinates the document that you've downloaded. Confirming the checksum of a downloaded program can help check that the program you are installing is the thing that you need to install.
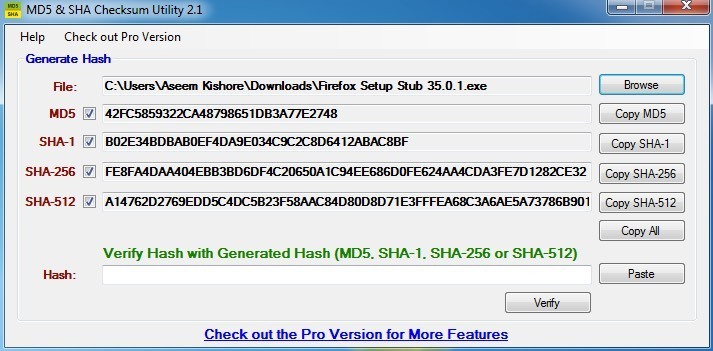
Step by step instructions to confirm the checksum of an installer record.
Related Posts

Tue, Mar 20, 2018 12:18 AM
Broadband Deals Money SubscriptionHow Much You Are Pay Per Minute For Your Streaming
Are we happy paying subscriptions?
Tue, Mar 20, 2018 12:44 AM
Technology Broadband InstallationInternet Provider Installation FAQs
Guide to Internet Provider Installation

Fri, Jul 6, 2018 7:04 PM
Eco-FriendlyWhere to recycle your technology hardware!
Easy tips on recycling your old computers and phones

Fri, Dec 6, 2019 4:22 PM
SafetyAlways Check the Website You Visit
Knowing the Threat

Fri, Dec 6, 2019 6:47 PM
SafetyTerrifying Cybercrime Figures
The internet allows us to connect with each other from all over the world, find the answer in a matter of seconds to almost every question, order food, get directions, send pictures, and so much more.